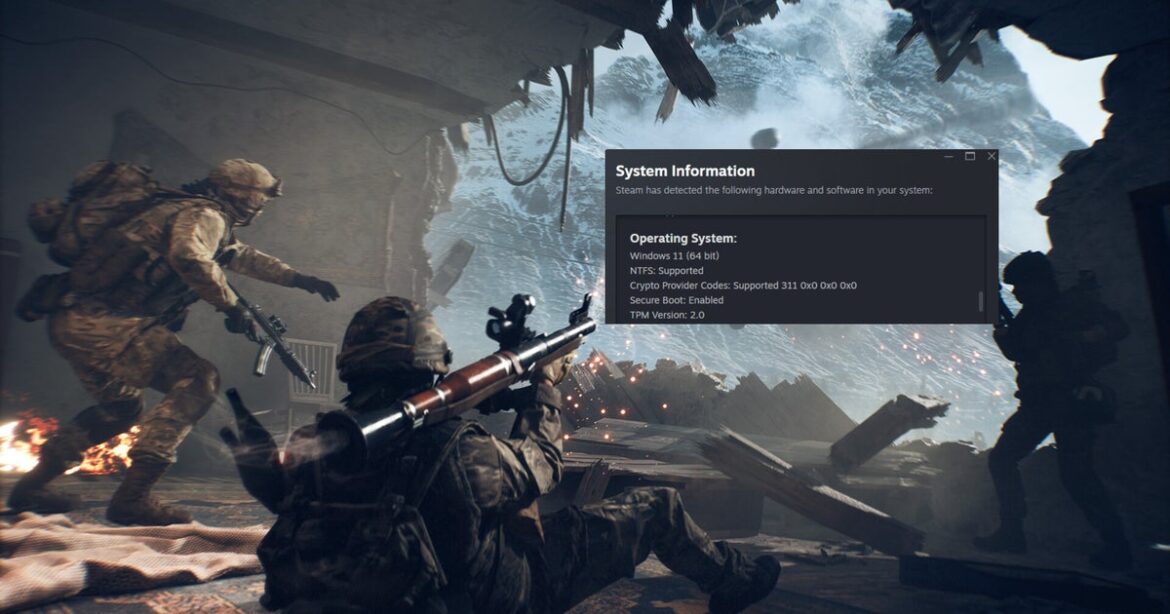
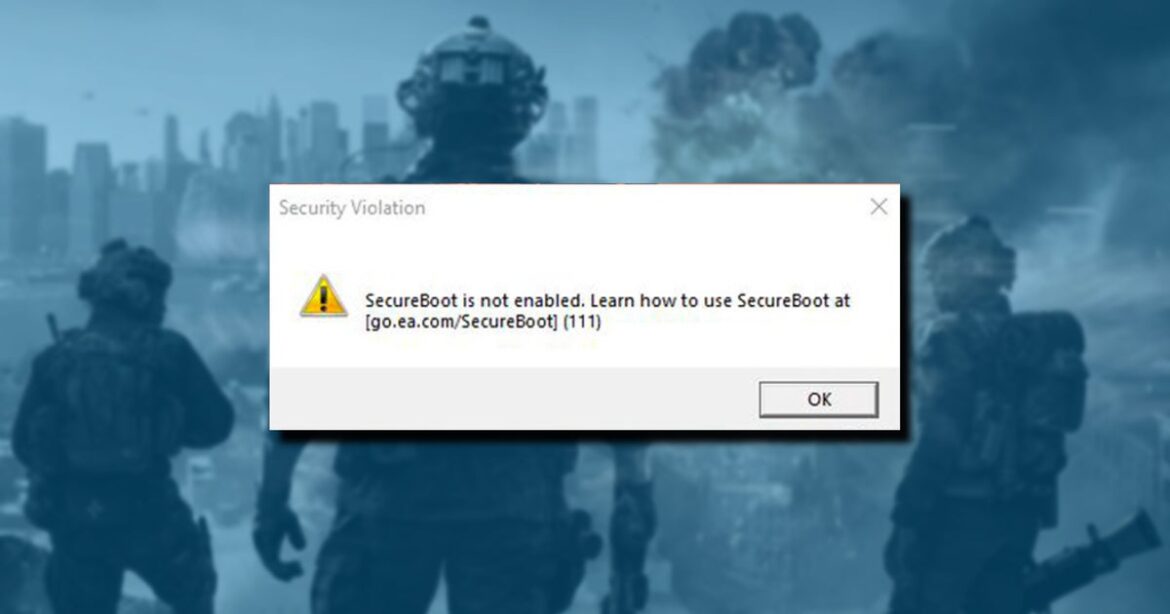
As mentioned above, you’ll need TPM 2.0 and Secure Boot set on your PC to play the Call of Duty: Black Ops 7 beta. Since that can get kind of technical, the team has put together a video to help you get that rectified. Check it out below, along with our hands-on preview from COD: NEXT!
We went hands-on with Call of Duty: Black Ops 7 at Call of Duty NEXT — A returning player’s perspective
It’s a wild ride filled with bullets
The Call of Duty: Black Ops 7 Multiplayer beta kicks off this week, starting with Early Access tomorrow for players who have pre-ordered the game, and then October 5 for all players.
For players on PC, in order to get their PC compliant today with TPM 2.0 and Secure Boot, the team has put together a quick tutorial that shows how to enable critical security settings so they can jump into the beta and full game at launch with ease.
Check out the video here.
This is part of Call of Duty’s detailed support guides to enable these two critical features, bringing players on the journey toward the most robust protections in gaming. The support hub also includes helpful guides for the top ten motherboard manufacturers used by the Call of Duty community. The entire, detailed step-by-step guide, motherboard guides, and new tutorial video are available at https://support.activision.com/tpm
Stay tuned to GamingTrend for more Call of Duty: Black Ops 7 news and info!
Share this article
The link has been copied!
Affiliate Links